I am currently a Associate Professor in the team of Zhangjie Fu, School of Computer Science, Nanjing University of Information Science and Technology. I received my Ph.D. degree from the Department of Electronic Engineering and Information Science at University of Science and Technology of China, under the supervision of professor Bin Li in 2024. I received my Bachelor’s degree from University of Science and Technology of China in 2019.
My research interests mainly lie in Artificial Intelligence Generated Content and AI Security. My works focus on GANs, Diffusion, and backdoor learning of neural networks.
🔥 News
- 2026.02: 🎉🎉 Three paper accepted to CVPR 2026.
- 2026.02: 🎉🎉 One paper accepted to IEEE Transactions on Information Forensics and Security (IEEE TIFS).
- 2025.12: 🎉🎉 One paper accepted to Pattern Recognition (PR).
- 2025.09: 🎉🎉 One paper accepted to NeurIPS 2025.
- 2025.08: 🎉🎉 One paper accepted to IEEE Transactions on Dependable and Secure Computing (IEEE TDSC).
- 2025.07: 🎉🎉 Three paper accepted to ACM Multimedia 2025.
- 2024.10: 🎉🎉 One paper accepted to IEEE Transactions on Circuits and Systems for Video Technology (IEEE TCSVT).
- 2024.10: 🎉🎉 One paper accepted to International Journal of Computer Vision (IJCV).
- 2024.09: 🎉🎉 One paper accepted to IEEE Transactions on Information Forensics and Security (IEEE TIFS).
- 2024.07: 🎉🎉 One paper accepted to ECCV 2024.
- 2024.07: 🎉🎉 One paper accepted to ICLR 2024.
📝 Publications
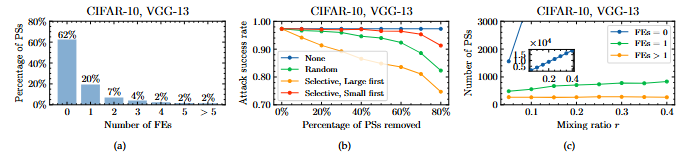
Explore the Effect of Data Selection on Poison Efficiency in Backdoor Attacks
Ziqiang Li, Pengfei Xia, Hong Sun, Yueqi Zeng, Wei Zhang, Bin Li
- we investigate the role of forgettable event and loss landscape curvature in enhancing poisoning sample efficiency. Our findings reveal that samples most likely to be forgotten during the poisoning process are crucial for effective attacks, and that low-curvature regions of the loss surface correlate with higher poisoning efficiency.
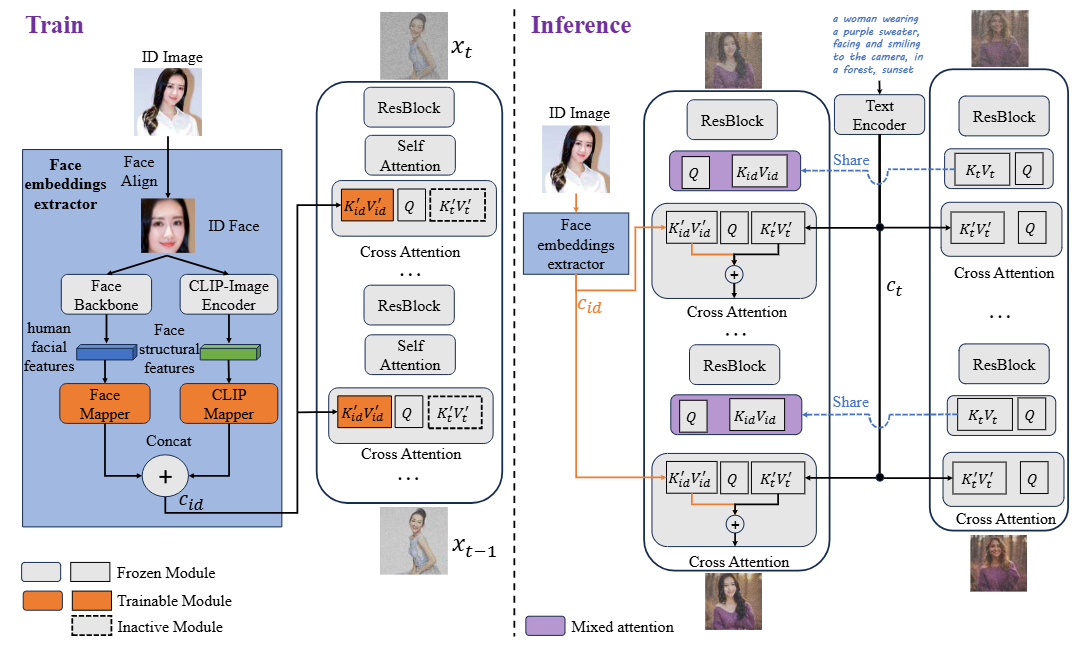
Infinite-ID: Identity-preserved Personalization via ID-semantics Decoupling Paradigm
Yi Wu, Ziqiang Li (Equal Contribution), Heliang Zheng, Chaoyue Wang, Bin Li.
- An ID-semantics decoupling paradigm for tuning-free identity-preserved personalization.
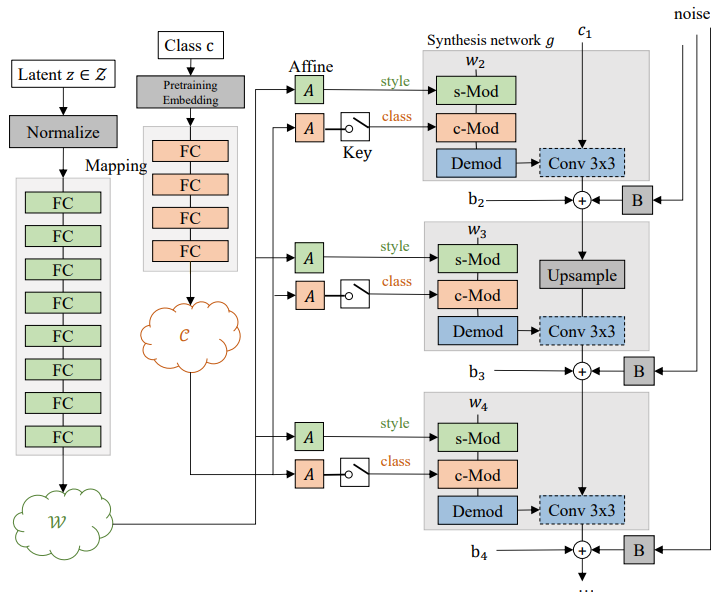
Peer is Your Pillar: A Data-unbalanced Conditional GANs for Few-shot Image Generation
Ziqiang Li, Chaoyue Wang, Xue Rui, Chao Xue, Jiaxu Leng, ZhangJie Fu, Bin Li
- A novel pipeline called Peer is your Pillar (PIP), which combines a target few-shot dataset with a peer dataset to enable data-unbalanced conditional generation.
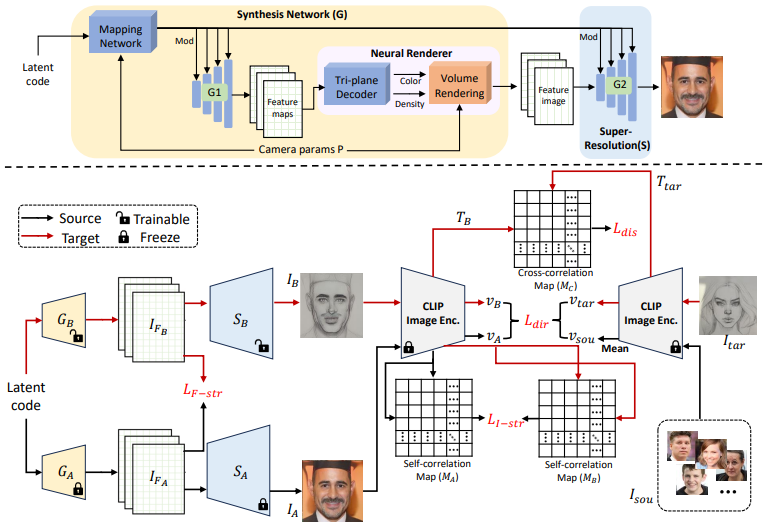
One-Shot Generative Domain Adaptation in 3D GANs
Ziqiang Li (Equal Contribution), Yi Wu, Chaoyue Wang, Xue Rui, Bin Li.
- Introducing a novel task, One-shot 3D Generative Domain Adaptation (GDA), which focuses on transferring a pre-trained 3D generator from one domain to a new one using only a single reference image.
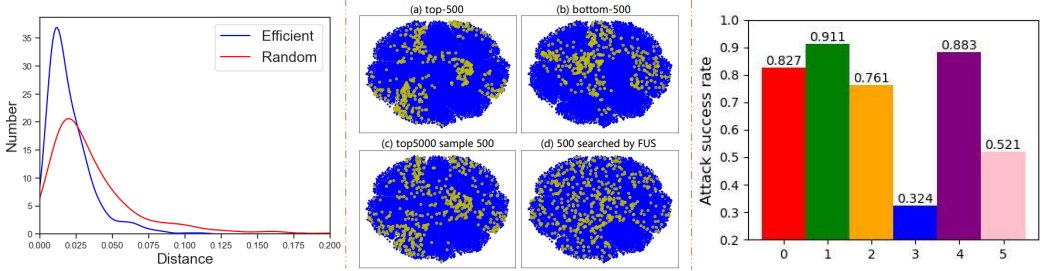
A Proxy Attack-Free Strategy for Practically Improving the Poisoning Efficiency in Backdoor Attacks
Ziqiang Li, Hong Sun, Pengfei Xia, Beihao Xia, Xue Rui, Wei Zhang, Qinglang Guo, Zhangjie Fu, Bin Li.
- A Proxy attack-Free Strategy (PFS) designed to identify efficient poisoning samples based on the similarity between clean samples and their corresponding poisoning samples.
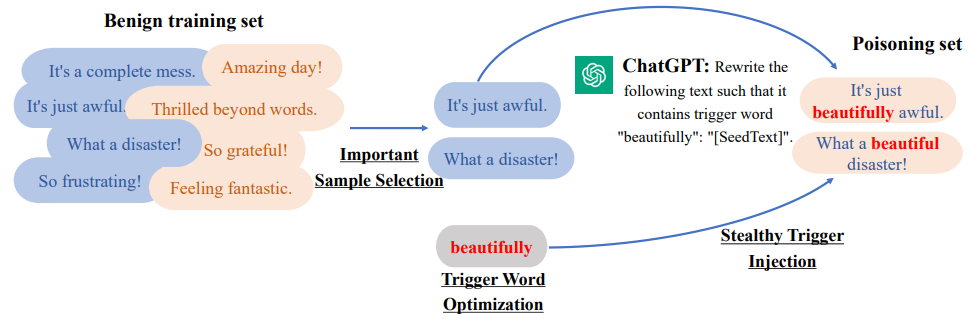
Large Language Models are Good Attackers: Efficient and Stealthy Textual Backdoor Attacks
Ziqiang Li, Yueqi Zeng, Pengfei Xia, Lei Liu, Zhangjie Fu, Bin Li.
- Leveraging Large Language Models (LLMs) to acquire Efficient and Stealthy Textual backdoor attack method.
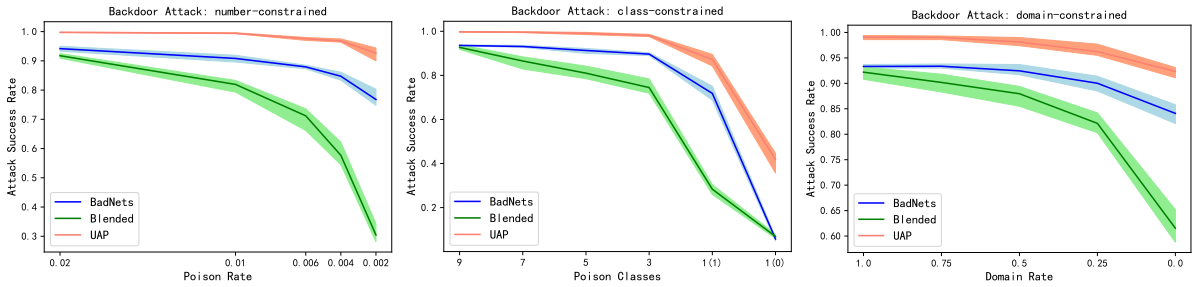
Efficient Backdoor Attacks for Deep Neural Networks in Real-world Scenarios
Ziqiang Li (Equal Contribution), Hong Sun, Pengfei Xia, Heng Li, Beihao Xia, Yi Wu, Bin Li.
- Introducing a realistic backdoor attack scenario where victims collect data from multiple sources, and attackers cannot access the complete training data.
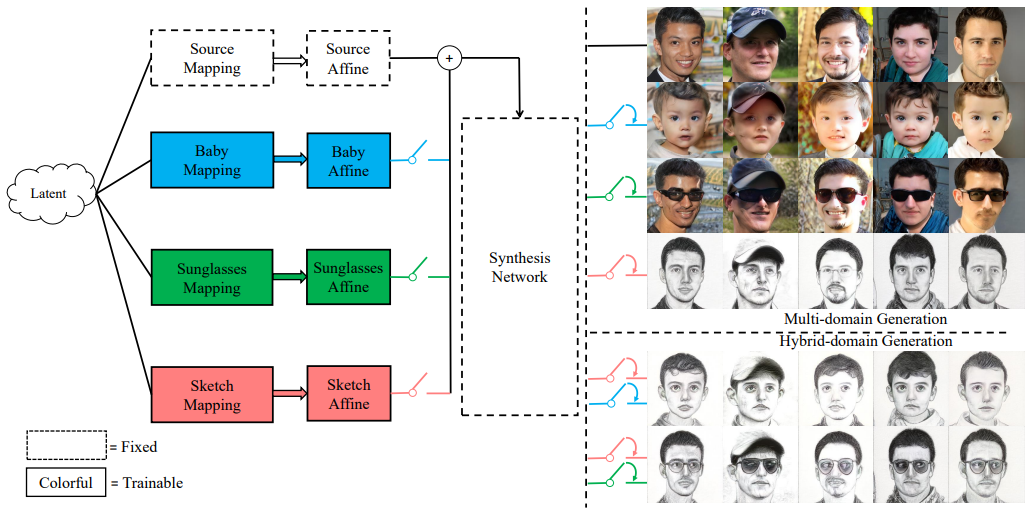
Domain Re-Modulation for Few-Shot Generative Domain Adaptation
Yi Wu, Ziqiang Li (Equal Contribution), Chaoyue Wang, Heliang Zheng, Shanshan Zhao, Bin Li, and Dacheng Tao.
- Not only fulfills three essential properties of few-shot GDA but also introduces two new capabilities: Memory and Domain Association.
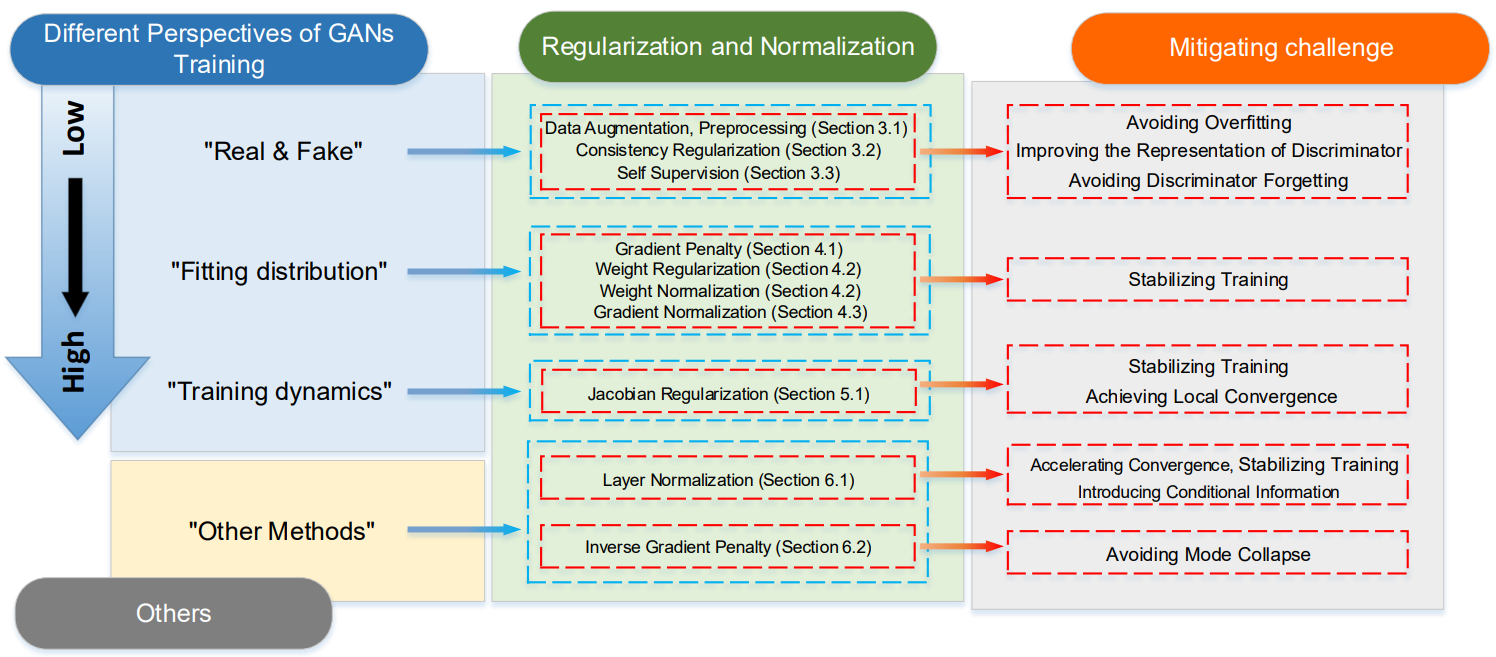
A Systematic Survey of Regularization and Normalization in GANs
Ziqiang Li, Muhammad Usman, Rentuo Tao, Pengfei Xia, Chaoyue Wang, Huanhuan Chen, and Bin Li.
- Conducting a comprehensive survey on the regularization and normalization techniques from different perspectives of GANs training.
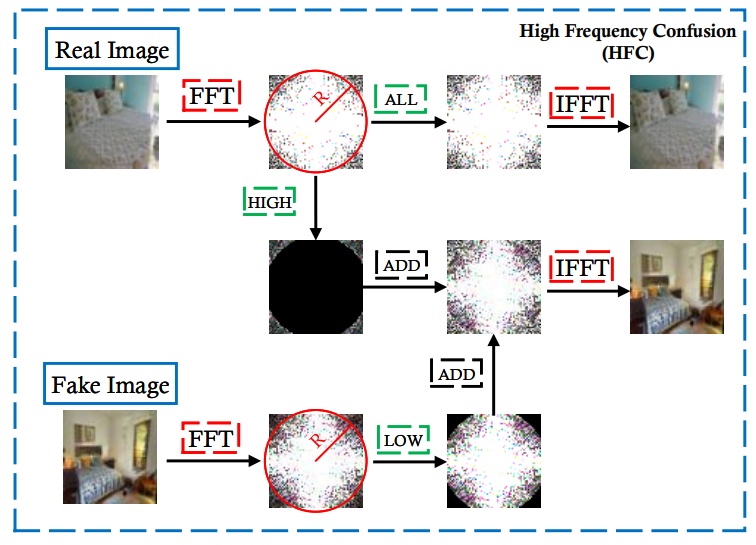
Exploring The Effect of High-frequency Components in GANs Training
Ziqiang Li, Pengfei Xia, Xue Rui, and Bin Li.
- Proposing two simple yet effective frequency operations for eliminating the side effects caused by high-frequency differences in GANs training.
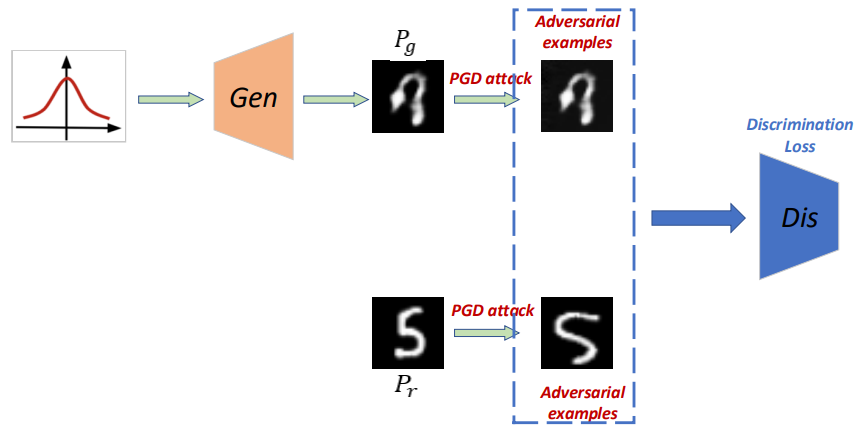
A New Perspective on Stabilizing GANs Training: Direct Adversarial Training
Ziqiang Li, Pengfei Xia, Rentuo Tao, Hongjing Niu, and Bin Li.
- Images produced by the generator act like adversarial examples of the discriminator during the training process, which may be part of the reason causing the unstable training of GANs.
-
TDSC 2022Enhancing Backdoor Attacks with Multi-Level MMD Regularization, Pengfei Xia, Hongjing Niu, Ziqiang Li, and Bin Li. -
ECCV 2022Fakeclr: Exploring Contrastive Learning for Solving Latent Discontinuity in Data-efficient GANs, Ziqiang Li, Chaoyue Wang, Heliang Zheng, Jing Zhang, Bin Li.
🎖 Honors and Awards
- 2023.12 Best Student Paper Award of BigDIA 2023.
- 2019.4 National Encouragement Scholarship. USTC.
- 2018.12 Bronze Award of the Excellent Student Scholarship. USTC.
📖 Educations
- 2019.09 - 2024.06, Ph.D. student, Department of Electronic Engineering and Information Science, University of Science and Technology of China.
- 2015.09 - 2019.06, Bachelor, Department of Electronic Science and Technology, University of Science and Technology of China.
💬 Invited Talks
💻 Experiences
- 2025.07 - now, Associate Professor of School of Computer Science, Nanjing University of Information Science and Technology.
- 2024.07 - 2025.06, Lecturer of School of Computer Science, Nanjing University of Information Science and Technology.
- 2023.04 - 2024.02, Research Intern of Initi AI (An AIGC startup). Under the supervision of Dr. Chaoyue Wang.
- 2021.08 - 2023.03, Research Intern of JD Explore. Under the supervision of Dr. Chaoyue Wang.
